Day 108: Building Tenant-Specific Configurations
Per-Tenant Customization Capabilities for Enterprise Log Processing
Youtube Video:
Today’s Build Agenda
You’ll implement a sophisticated tenant configuration system that allows each organization using your distributed log platform to customize their experience. We’ll build:
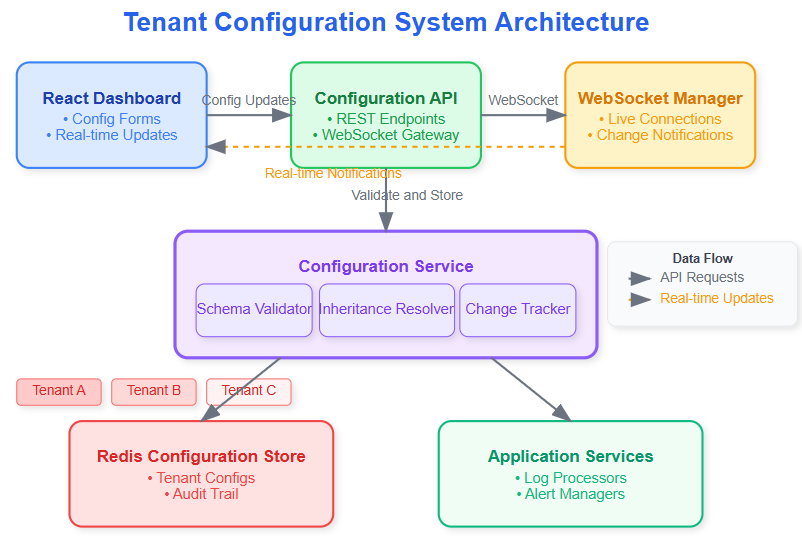
Dynamic Configuration Engine - Real-time config updates without restarts
Hierarchical Config Management - Global, tenant, and user-level settings
Configuration Validation - Type-safe config with business rule enforcement
Live Config Dashboard - React interface for tenant administrators
Config Versioning - Track changes and enable rollbacks
Why Tenant Configurations Matter
Enterprise SaaS platforms like Datadog and Splunk serve thousands of organizations, each with unique logging requirements. A healthcare company needs HIPAA-compliant retention policies, while a fintech startup requires real-time fraud detection alerts. Generic configurations create friction; personalized settings drive adoption.
Your multi-tenant log platform becomes truly enterprise-ready when tenants can customize log parsing rules, retention periods, alert thresholds, and integration endpoints without requiring engineering support.
Working Code Demo:
Core System Design Concepts
Configuration Hierarchies
Modern multi-tenant systems use hierarchical configuration inheritance. Global defaults ensure system stability, tenant overrides enable customization, and user preferences provide personal touches. This three-tier approach balances flexibility with operational safety.
Dynamic Configuration Loading
Static configuration files require application restarts for changes. Dynamic systems watch configuration stores and hot-reload settings, enabling real-time tenant customization without service disruption.
Configuration Schemas
Type-safe configurations prevent runtime errors. JSON Schema or similar validation ensures tenant customizations comply with system constraints while providing clear error messages for invalid settings.
Context in Distributed Log Processing
Your tenant-specific configurations enhance the isolation layer built in Day 107. While resource quotas limit what tenants can consume, configurations control how tenants experience your platform. Together, they create a complete multi-tenant foundation.
This system prepares for Day 109's automated tenant onboarding by establishing configuration templates and validation rules that new tenants inherit automatically.